Bring Your Own Key (BYOK):
A Comprehensive Guide
Is your business utilizing a public cloud infrastructure and striving to secure data from cloud service providers and other shared teams? If so, Bring Your Own Key (BYOK) is for you. Designed as a security model to allow organizations to gain control over data security.
What is Bring Your Own Key (BYOK)?
BYOK is an enhanced encryption practice where organizations have the ability to encrypt and decrypt data as per their needs and requirements. In simple terms, think of BYOK as a rental space where you have access to everything except ownership of the key.
Unlike traditional models where cloud service providers generate and store encryption keys, the BYOK gives organizations the ability to create, generate and manage encryption keys that are used to secure and protect their data. While organizations need to transfer the encryption key to the respective cloud service providers, it makes no difference as the organization holds the responsibility for key management operations like monitoring BYOK key rotation frequency, managing key distribution phases, and streamlining key revocation procedures.
With the BYOK solution, organizations can protect their sensitive data and applications by segmenting them even in third-party infrastructure, as they have complete control over encryption keys. While its uses, cases and benefits are many, let us first explore a little history and evolution of BYOK encryption.
History and Evolution of Bring Your Own Key
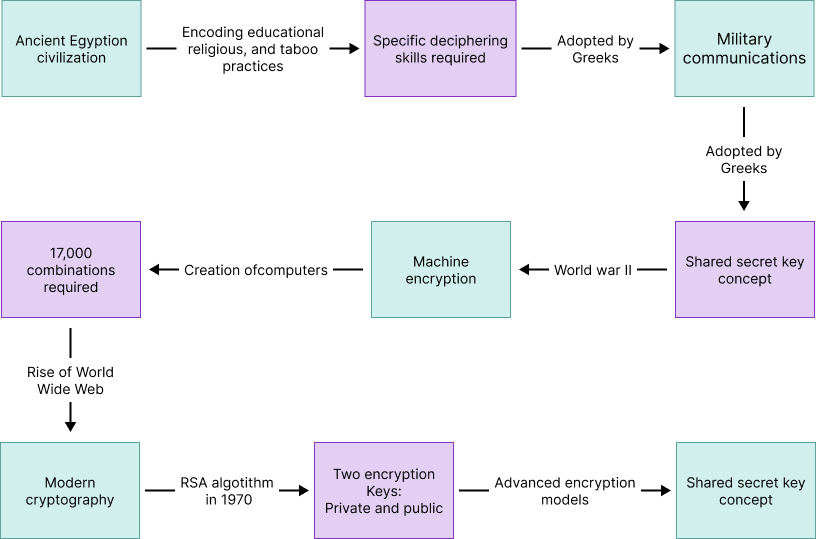
- In Egyptian civilization, encoding educational, religious, and taboo practices was documented in secretive ways, requiring specific deciphering skills to interpret them.
- Later, the Greeks utilized this approach to hide military communications through a device known as the scytale, which involved wrapping a strip of parchment around a staff to reveal a message only readable on a matching staff, introducing the concept of a shared secret key.
- World War II changed the course of encryption, as it was the beginning of machine encryption. It was during this time that computers came into existence. The encryption created using those computers would require trying nearly 17,000 combinations.
- The rise of World Wide Web gave birth to today’s modern cryptography, the RSA algorithm in 1970, which had two encryption keys, one private and one public, underpinning the security of digital communications. Thus, this marks a significant evolution for today’s advanced encryption models, like BYOK.
Verify the Authenticity and Integrity of your Documents
Explore our Digital Signature Solutions

Established as a security practice where organizations create, manage and maintain their own encryption keys for data in public cloud applications. This approach provides comprehensive control over the encryption keys for the organizations, leading to end-to-end visibility of applications and other activities. As the adoption of public cloud infrastructure seems to be cost-effective, too many organizations heading to a common infrastructure are subject to some serious threats in terms of unauthorized access, compliance risks, data privacy and data integrity.
BYOK vs. Traditional Encryption
When compared to traditional key management, BYOK allows organizations to take full control of their security posture in a shared environment, reducing the fear of data loss and breaches. Let’s analyze BYOK vs. traditional encryption for a detailed understanding of why BYOK security is the most preferred approach among organizations.
Ownership and control
Traditional key management: In this practice, the service provider generates, manages and stores the key responsible for the encryption and decryption of data. The service provider handles all aspects of key management, right from creation to revocation to storage within their infrastructure, known as Key Management Service (KMS).
BYOK: Customers generate their own key encryption through methods like Hardware Security Modules (HSM) or Key Management Service (KMS). This way, customers can take full advantage of key management functions like creation and maintenance, protecting their data and applications in a way they need and require.
Security Responsibility
Traditional Key Management: As the service provider owns the full rights to the key encryption, they will ensure robust security measures like access controls, encryption and physical security like implementing surveillance are incorporated as per every shared application’s needs and requirements.
BYOK: On the other hand, customers having full control over the key encryption can tailor security protocols, custom policies and procedures that align with current threats and breaches, which can later be modified or customized according to various threats and vulnerabilities.
Data privacy and compliance
Traditional Key Management: Ensuring updated compliance and data regulation rules is important to secure and protect the data. Also, as customers have limited to no control over the provider’s key management, it is important to be on track with the latest security regulations, compliance certifications and audits.
BYOK: By overviewing key encryptions and other safety protocols, BYOK key management empowers organizations to keep track of compliance risks, regulatory adherence and other audits. This way, customers can ensure their data is not just protected but also well aligned with the latest regulatory measures.
Integration and Compatibility
Traditional key management: With key encryption managed within the service provider infrastructure, a seamless and straightforward BYOK integration is enabled.
BYOK: With customers managing key encryption systems, integration with the service provider’s infrastructure can be quite challenging and complex. While creating key encryption, it is recommended to ensure that it will be compatible with the service provider’s infrastructure.
Risk Management
Traditional key management: Managing unauthorized access and other security risks solely depends on the service provider for they are the owners of key encryption systems.
BYOK: Whereas in BYOK, customers have unlimited control over data integrity and security. Also, they can implement security policies according to their own convenience, leading to enhanced and streamlined risk mitigation measures.
Fundamentals of Bring Your Own Key
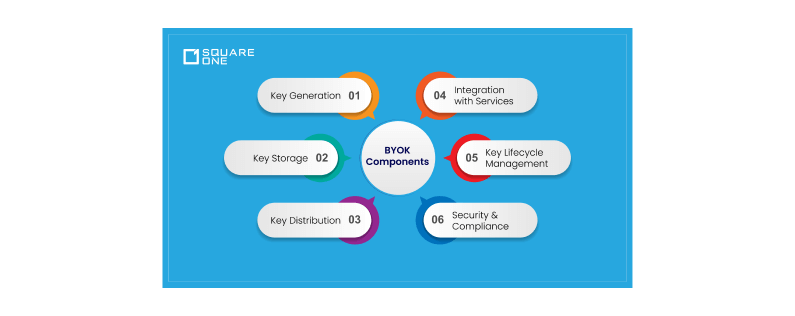
Components of BYOK
So what makes up BYOK?
- Key Generation
- Key Storage
- Key Distribution
- Integration with Services
- Key Lifecycle Management
- Security and Compliance
Key Generation
As a primary aspect of the BYOK framework, organizations generate keys of their own to encrypt and decrypt data that are robust and secure against attack. Key generation is achieved through the following three processes
- Using cryptographic algorithms like AES or RSA, which is considered to be a secure method of key generation
- Through physical devices like Hardware Security Modules (HSM) that generate and store encryption keys securely, providing a high level of protection against unauthorized access and tampering.
- Finally, through a software-based service that can be integrated with cloud platforms but is controlled by the organization to maintain security and compliance.
Key Storage
The next component in the BYOK framework is key storage, focusing on securing the generated encryption key from unauthorized access and control
- Access controls like role-based authentication and policies are established to ensure that only authorized users can access the encryption keys.
- The software service used for generating keys implements auditing capabilities and access controls, offering secure storage options.
Key Distribution
This component helps in delivering the generated key to the cloud service or application for data encryption and decryption. By
- Transmitting the encrypted key over secured and encrypted channels like Transport Layer Security (TLS) that are tamper-proof and robust.
- Wrapping or encrypting key over another key before transmission, ensuring only authorized access to the keys.
Integration with Services
Being compatible with cloud platforms and APIs provides seamless import and usage, ensuring that the encryption and decryption processes function correctly. The integration of cloud infrastructure with BYOK is a significant component.
- Utilizing Application Programming Interfaces (APIs) to import, manage and interact with customer managed encryption keys.
- Establishing secure communication channels between the key management and the cloud service APIs.
Key Lifecycle Management
As a measure to take care of the keys and ensure they are properly handled, this component in BYOK plays an important role.
- Regularly replacing keys enhances its security posture and reduces the risk of tampering.
- Withdrawing keys that are no longer in use or those that have been compromised on the security front.
- Implementing backup plans in the event of accidental deletion or system failure.
- Continuously monitoring the usage of keys and maintaining an audit will help track down compliance risks and illlegal access.
When compared to traditional key management, BYOK allows organizations to take full control of their security posture in a shared environment, reducing the fear of data loss and breaches. Let’s analyze BYOK vs. traditional encryption for a detailed understanding of why BYOK security is the most preferred approach among organizations.
Security and Compliance
As a final component of the framework, BYOK compliance ensures that the generated key adheres well to security and compliance regulations through the following ways
- Implement robust security features like multi-factor authentication, access controls, and encryption.
- Check for compliance, like HIPPA, GDPR, PCI-DSS etc.
- Maintain control over key management with respect to local data protection laws and data sovereignty.
Primary Actors in BYOK Encryption Model
While the key components of BYOK have been explored, let’s move on to the key players in the framework
Customer/organization: They are responsible for the creation, generation, and management of encryption keys.
Key Management System: Provides the technology and infrastructure to securely generate, store and manage encryption keys.
Cloud Service Provider: Host the cloud services or applications where data encryption and decryption take place.
Hardware Security Module Vendor: Provider of HSM, a physical device that offers high-end security for key protection.
Compliance Authorities: Empower organizations to set compliance standards for data protection, encryption and key management.
Internal IT and Security Team: Play a vital role in configuring key management systems, integrating keys with cloud services, and implementing security policies within the BYOK framework.
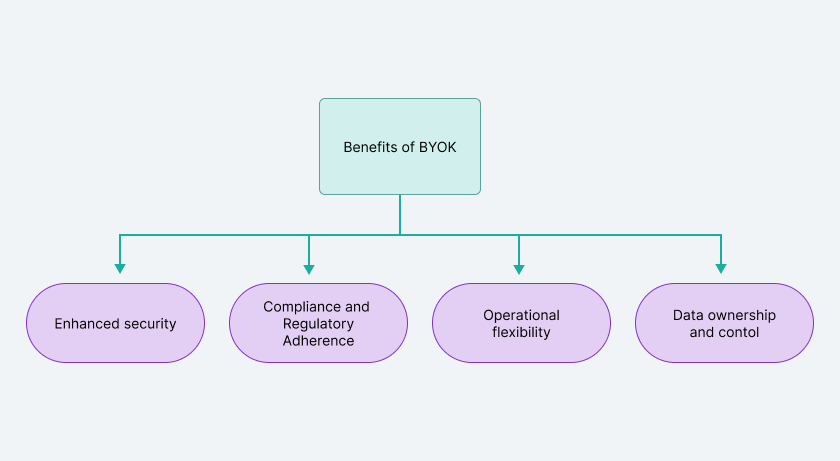
Merits of BYOK
Evaluating an encryption model largely depends on the key factors it offers to organizations. Let’s examine these factors
- Enhanced Security
- Compliance and Regulatory Adherence
- Operational Flexibility
- Data Ownership and Control
Enhanced security
One of the significant benefits of the BYOK solution is its ability to offer enhanced and increased security measures to organizations utilizing a shared environment in the cloud.
Consider a financial entity using BYOK to encrypt sensitive data in the cloud. In the event of any security breach at the cloud provider, there is no compromise to the keys generated or managed by the entity. Thus proving that BYOK in financial services can be an enhanced and secure addition for the organization in safeguarding and protecting unauthorized access.
Compliance and Regulatory Adherence
Prioritizing compliance and regulatory adherence is crucial for organizations operating with stringent data protection requirements. Any failure to uphold the latest rules and regulations would lead to reputational damage, severe penalties and fines.
Consider a healthcare organization struggling to comply with HIPAA regulations and secure patient data in the cloud. By implementing the BYOK solution, the organization can gain control and access to protect patient data. This control ensures that encryption keys are managed securely and in accordance with HIPAA’s encryption requirements. BYOK in healthcare also facilitates auditing and monitoring of key usage, providing transparency and accountability in data protection practices.
Operational flexibility
With BYOK, tailoring security protocols and encryption policies ensures optimal protection for different types of data and applications. Also, organizations can customize their key management practices, such as key rotation frequency, revocation procedures and access controls, reducing the risk of data breaches and unauthorized access.
Consider a retail firm utilizing a shared environment to store customer data and their transaction patterns. It also uses the same infrastructure to store the data of employees working in various locations. With BYOK, the firm can balance the encryption policy and security access by using strong encryption methods for customer data and light encryption for employee data. This way, the organization can foster operational efficiency, enhance security and scale protocols when needed.
Data ownership and control
Managing the encryption keys allows organizations to maintain ownership and control over data privacy and data sovereignty, ensuring data is subject to the laws and regulations of their jurisdiction and minimizing access by unauthorized personnel and even cloud service providers.
Consider a multinational firm building confidential software codes and looking to store them in the cloud. With BYOK, they can secure their proprietary code from illegitimate access and maintain data sovereignty and compliance with local rules and regulations, reducing the risks of compliance and regulatory standards
Elevate your organization’s efficiency, agility, and customer satisfaction
Leverage our Business Process Management solutions

While the benefits have been explored, it is time to analyze the deployment measures of BYOK
Strategically Implementing Bring Your Own Key (BYOK) Encryption
The first step in implementing BYOK depends on your Key Management Service provider. Having a seamless and straightforward integration with cloud platforms is all based on the capabilities and potential of your Key Management Service provider. Choosing the right Key Management Service provider involves evaluating certain criteria that align with your organizational security needs, compliance requirements and other goals. Let’s have a quick look at the essential conditions that support selecting the Key Management Service provider of your organization’s choice.
Conditions to look in a KMS Provider
Security Features: Assessing the key management functionalities like key rotation frequency, key revocation duration, and storage methods of the provider helps provide insights about their security potentials and facilities.
Integration Capability: Easing the integration process with the organization’s existing infrastructure, cloud applications and other cloud platforms through APIs and SDKs serves as a crucial condition for the right Key Management Service provider.
Scalability & Performance: Supporting organizations data volume and growing complexity along with latency rate, throughput and flexible key management operations plays an important role during high availability needs and disaster management.
Compliance & Regulation: Ensuring strict adherence to data protection laws like GDPR, HIPAA, PCI-DSS and other industry specific regulations fosters a strong sense of credibility and trust.
Cost & Pricing: Reviewing key management plans like usage-based pricing, subscription plans and additional fees for key management operations should be analyzed and considered before jumping to the selection. Also, consider factors like the total cost of ownership (TCO) over time, including implementation costs, ongoing maintenance, and support.
Evaluating Popular KMS Providers
Here’s a comparison on the major Key Management Service providers in the market.
Particulars | Azure Key Vault | AWS | Google Cloud | IBM Key Protect |
|---|---|---|---|---|
Service Type | Provides end-to-end key management | Facilitiates cloud service for key management | Centralized key management | Comprehensive key management |
Integration | With Azure services | With Amazon services | With Google services | With IBM services |
Key Management | Creation, import and control of keys | HSM-powered key management | Creation, import and control of keys | Entire Key lifecycle management |
Complaince Certification | Adheres to FIPS 140-2, HIPAA, PCI-DSS | Supports FIPS 140-2, GDPR, ISO/IEC 2700 | Complies with FIPS 140-2, PCI-DSS | Ensures FIPS 140-2, GDPR, HIPAA regulation compliance |
Data Encryption | Both at rest and transit | Both at rest and transit | Both at rest and transit | Both at rest and transit |
Now that we have selected the right Key Management Service provider, all that remains is to follow a few best practices that ensure seamless cloud service integration.
Proven Practices for Cloud Service Integration
Step 1: Start by analyzing the Key Management Service provider and their integration capability. This is a crucial step, as their support for external imports and interoperability is essential for a straightforward approach
Step 2: As a next step, be responsible for handling key management operations like key rotation, enhancing access controls, key revocation, and customizing security policies as per data and application requirements.
Step 3: Now that the encryption keys are generated, it is important to look into secure storage methods. Using devices like HSMs helps enforce strong security protocols for keys, preventing unauthorized users.
Step 4: Make sure to take care of the key rotation process for frequent encryption updates, which ensures the key is robust and secure enough to resist attacks and breaches.
Step 5: Set up a monitoring and tracking facility for key usage and key performance, and also document all policies related to BYOK, like configuration, encryption details, and access control information.
Step 6: Conduct test integration with cloud platforms and check for issues and challenges. If any, resolve them and make sure that they perform efficiently and error-free. Also, perform periodic evaluations and reviews of the key management operations. This will help provide insights on integration enhancements in the future.
BYOK in Multi-Cloud Environment
Managing encryption keys across various cloud service providers helps provide consistent and uninterrupted data security services. However, managing them can be quite challenging and crucial. Here are a few challenges that occur with BYOK in hybrid cloud.
Unified Key Management: Managing keys across multiple- clouds increases operational complexity and lowers performance, for it is quite concerning for organizations to manage the lifecycle of encryption keys like key rotation, key revocation and key management.
Interoperability: A single encryption key for various cloud services facilitates a struggle for organizations due to the different types of APIs, SDKs and other programming interfaces available at different cloud service providers.
Compliance and Sovereignty: Ensuring compliance with diverse regulatory requirements and data sovereignty laws across various jurisdictions can be difficult, as different cloud providers may have different standards and practices.
Security Risks: Having an extended surface attack in a multi-cloud environment can be a huge threat for organizations if they fail to update the audit log or enhance their encryption policies and security protocols.
To help organizations with BYOK in multi-cloud environment, a few practices like the following can be implemented.
Uniform Key Policies: Applying consistent encryption policies across all platforms helps standardize security protocols and enforcement.
Automate Key Management: Using BYOK automation tools and scripts to manage key lifecycle processes as they expire or become vulnerable to threat attacks.
Conduct Regular Audits: Addressing gaps and issues of compliance and regulatory adherence on a regular basis helps comply with regulatory requirements on time.
Data Segmentation: Separating sensitive and confidential data from non-sensitive data helps enforce security policies accordingly. This way, organizations can apply robust security rules to applications of high value.
Disaster Recovery Planning: Developing disaster recovery methods helps organizations get back encrypted procedures that can be restored quickly and securely in case of a failure or data breach.
Examining the role of BYOK helps organizations identify how its use cases enhance data security, ensure regulatory compliance, and provide greater control over encryption keys within cloud environments.
Exploring the Versatile Applications of Bring Your Own Key
BYOK in Regulated Industries
Sectors like healthcare, government, finance and cross-border transactions are a few industries that are operated under strict regulations owing to the presence of sensitive information from users, clients and government departments. So the implementation of the BYOK solution in such highly regulated environments plays a crucial role in securing and protecting data and critical applications from ill-legal access and malicious attackers. Here is a case study involving two global countries with stringent data protection laws, the USA and the European Union, showing the inadequacy of data protection regulations.
Any personal data from the EU to be transferred needs to follow GDPR rules and ensure that the data is robust enough against attacks and decryption. In this case, an EU operator used a Google Analytics service provider based in the US while transferring the data to the US. This empowered the US agency to decrypt the data, as the operator relied on Standard Contractual Clauses (SCCs), meaning the encryption of data at rest. The Austrian Data Protection Authority ruled on this and stated that the transferred data did not meet the regulatory standards of protection as in the European Economic Area (EEA). This incident has given rise to the utilization of BYOK in cases where data protection rules and laws are insufficient, leading to the decryption of data and applications.
BYOK in SaaS & Enterprise Applications
The need for secure and performance-oriented document management systems has heightened among sectors. This is evident from the below BYOK case study by Antimatter for one of the Fortune 50 companies, Ironclad, a contract lifecycle management platform.
The customer of Ironclad demanded full control over data security along with customer encryption, which led the contract lifecycle management platform to seek Antimatter’s assistance. They helped build the BYOK solution within weeks, empowering Ironclad to offer advanced security functionalities to users that displayed excellent security performance, audit logging and transparency with minimal impact on the application’s performance. Thus, BYOk for SaaS creates a more secure and safe document management platform for Ironclad users.
Having explored the use cases and benefits of BYOK, let’s delve into the challenges and solutions, helping organizations gain a deeper understanding of its implementation
Addressing BYOK Roadblocks with Effective Solutions
The implementation of BYOK is, of course, an essential solution for organizations looking to protect and secure their data and applications in the cloud. But on the other hand, the challenges it poses regarding key management, security risks and integration with legacy systems are something that needs to be addressed prior to the implementation process. Let’s take a look at what the BYOK challenges are and how they can be overcome.
Key Management Challenges: As a known fact, encryption keys are the gateways for malicious attackers and hackers to sensitive information. So it is important to take care of these keys in a safe and secure manner that is robust and strong enough against data breaches and attacks. Below are the important aspects to keep in mind for key management challenges
- Generating and distributing keys to parties needs to be safe and secure, without any compromise to their functionality and authenticity.
- Securing encryption keys in HSMs, key vaults or other storage devices that prevent unauthorized access, theft and loss of data.
- Implementing granular access controls, role-based access or least privileges that allow only authorized persons or users to operate the application or data.
Security risks: Every piece of data in today’s world is a revenue-generating insight that needs meticulous attention to safeguard. Exchanging encryption keys from organizations to cloud service providers poses a high chance for attackers to decrypt them and read data. Also, poor management of keys, such as no key rotation or the absence of updating key encryption policies, presents a great security threat that needs to be monitored. Here are a few mitigation measures for organizations to stay alert and notified.
- Employ end-to-end encryption methods for keys while transitioning them from organization to cloud service provider. Also, make sure to transit them through secure, encrypted channels like TLS.
- Use Security Information and Event Management (SIEM) tools to analyze logs for suspicious activities and potential security incidents.
- Conduct regular training and workshop sessions for employees on the importance of key management and its necessity in today’s digital world.
- Split the responsibilities for employees handling encryption keys. This leads to only authorized employees working around key management operations.
Integration with Existing Systems: Implementing BYOK, although it seems to be a streamlined process, requires certain compatibility with the existing infrastructure, for it is a modern approach that has advanced encryption policies, wide API support, and no constraints on devices and technologies. Whereas, existing infrastructure that is considered a legacy in terms of performance, dependency and operational efficiency needs to be renewed for a successful and seamless integration. Here are few considerations to make before implementing BYOK with a legacy system
- Having an encryption translator tool like wrappers or encryption gateways bridges the gap between BYOK and legacy systems.
- Developing alternative integration methods like APIs or SDKs or customizing them that suit both BYOK and legacy systems.
- Considering phased migration strategies that test and validate each function of legacy systems in alignment with the BYOK solution.
- Upgrading resource constraints like hardware or software helps legacy infrastructure elevate to the standards of BYOK solution.
User Training and Awareness: Educating users and employees on the significance and importance of the BYOK solution is a primary task for organizations preparing for BYOK implementation. From introducing the technical concept to communicating the functionality and use case of the tool, awareness and training sessions are necessary for they foster rapid knowledge transfer and efficient usage. By following the below practices, organizations can educate and create awareness.
- Conduct workshops and user training for BYOK by experts who can simplify the technical concept.
- Create awareness about the solution and its role for the organization.
- Establish continuous training programs that include online forums, webinars and sessions where users can actively interact and resolve queries and clarifications.
Moving forward, it is crucial to understand the advancements of BYOK, emerging trends, and how BYOK serves different settings.
Beyond Basics: Advanced Capabilities of Bring Your Own Key
The role of HSMs in BYOK
The role of HSMs in BYOK is crucial and significant, for they help with the secure generation and storage of encryption keys. They ensure that the encryption keys are never exposed by performing cryptographic operations like encryption, decryption and digital signatures in an environment away from the application. This way, HSMs help organizations stay away from unauthorized access and physical tampering. Thus, the integration of HSMs into BYOK provides an enhanced and high level of protection, facilitating a more advanced version of BYOK that is capable of being utilized in more advanced applications and environments.
BYOK in IoT Environment
IoT adoption is increasing among industries and manufacturing units for enhanced operational efficiency and performance. The implementation of IoT devices is improving human-machine interactions. At the same time, it is essential to secure the data generated through devices and sensors from malicious insiders and data hackers. The implementation of BYOK IoT can help industries address security issues promptly. Start with the integration of key management, then move on to device positioning for each IoT device with the necessary key encryptions from the Key Management Service.
Imagine a smart home device manufacturing company uses IoT devices to generate and transmit data. The implementation of BYOK helps homeowners create and manage their own encryption keys, facilitating comprehensive control and monitoring of personal data, audit logs and feed details. This ensures homeowners data is adequately protected even in the event of a security breach at the service provider’s cloud infrastructure.
BYOK in Big Data
Datasets that are sourced from multiple sources and are large, complex and vast to process using traditional methods are referred to as Big Data. Sectors like finance, government and healthcare all deal with Big Data, finding solutions that can enhance and improve the security and encryption of data. The role of BYOK Big Data encryption empowers organizations with full control over data integrity, security and sovereignty.
Imagine a banking sector receiving data from multiple sources that include credit card details, transaction processes, loan applications, and other user details on a daily basis. To streamline all data and secure it is time consuming and challenging. With the BYOK solution, the entity can create their own encryption keys that can be utilized to encrypt and enforce security policies that are robust and strong enough to fight data breaches and threat attacks. Also, it helps the banking sector stay ahead of security protocols, even if the cloud service provider’s infrastructure is breached or compromised.
Future Trends of BYOK
Zero Trust Models
As the name suggests, this is an advanced security approach that does not trust either internal or external personnel. It operates solely based on verification and authentication provided by the personnel trying to gain access to the data.
Machine Learning Integration
With ML integration into key management systems, organizations can learn more about key usage patterns, identify and set up key rotation frequencies and make other predictions in advance, leading to enhanced key management operations.
Blockchain for Key Management
A digital immutable record that can neither be altered nor deleted guarantees enhanced transparency and security for data integrity. With this functionality, organizations can keep track of all data entries related to key creation, distribution, revocation and retirement operations, providing a clear auditable trail of records supporting compliance regulations.
Interoperability Standards
With a standardized approach to integration, organizations can easily work across different cloud service providers. It also assists with easy migration and integration of encryption keys between various platforms, facilitating flexibility and operational efficiency.
Overall, BYOK future trends appear highly promising and advanced, enabling organizations to operate more efficiently and effectively
Looking for a powerful solutions to manage your enterprise information?
Explore our Enterprise content management capabilities

Introducing HYOK
Hold Your Own Key
The name is quite straightforward in stating what it means, holding or retaining encryption keys that organizations create, generate and store. In this case, organizations are not entitled to securely transfer the keys to a cloud service provider but rather have complete ownership of the keys. This way, businesses operating in sensitive and regulated environments can integrate BYOK for data privacy even while residing in a shared cloud environment.
In simple words, imagine HYOK as your own house, where you have full rights and control over the key access.
Significance of HYOK
Let’s analyze its benefits
Enhanced Security: This is the most significant functionality of HYOK, where organizations get to gain full control over who should visit their applications. This empowers organizations to prevent and protect their data from third-party interference.
Flexible Key Management: With HYOK, organizations can integrate their encryption keys with other advanced security systems, thereby assisting with key rotation, management and storage facilities.
Non-Accessible in Multi-Cloud Environment: Organizations utilizing multi-tenant environment and sharing the infrastructure with various organizations can be assured that their encryption keys are not accessed or compromised by other team members.
Business continuity: Organizations can overcome any disaster independent of cloud service failure, owing to the complete ownership of encryption keys and a robust disaster recovery procedure in place.
Adherence to Compliance: Stringent compliance with regulations and laws requires complete ownership of encryption keys and HYOK helps in establishing and maintaining on date compliance adherence for organizations operating in restricted environments.
Overall, HYOK presents a more enhanced security approach and optimized key management operations for organizations struggling to meet both ends.
While HYOK’s offerings are vast and significant, integrating them isn’t a cake walk. Gaining a brief knowledge of the challenges and the strategies to address them can help organizations stay aware and ahead.
Challenges and Strategies in Implementing HYOK
Increased responsibility: In HYOK, organizations bear the full responsibility of the encryption keys, leading to enhanced maintenance of encryption keys that include comprehensive security measures, robust encryption policies and other advanced measures, resulting in overhead charges.
Strategy: Utilizing dedicated key management hardware that encompasses all functionalities required for secured encryption, right from implementing policies to maintaining audit trails. This will increase security while minimizing overhead charges.
Scalability Issues: Having a key management operation that supports growing business needs like large volumes of data is quite challenging for organizations operating with the HYOK solution.
Strategy:
Leveraging cloud-native key management solutions can help organizations integrate with on-premise infrastructure, balancing scalability and interoperability challenges within control.
Key Availability and Performance: Managing a single encryption key for every platform and location can deter the performance of key management operations.
Strategy: Deploying redundant key management operations helps organizations maintain encryption keys only for certain periods of time. Also, optimizing key performance using high performance hardware elevates the lifecycle and retrieval algorithms, leading to improved performance.
Access Management: As organizations continue to have control over keys, it becomes difficult to have a single authorized user or personnel.
Strategy: Controlling users by implementing strict access through an authentication and verification approach ensures that only a few authorized users can handle and manage encryption keys. In this way, organizations can limit user access, detect malicious attackers and report on time.
BYOK vs. HYOK
Now that every aspect of HYOK has been addressed, let’s have a look at BYOK vs. HYOK
Particulars | BYOK | HYOK |
|---|---|---|
Control | Create and generate encryption keys, which are later securely transferred to the cloud service provider. | Have full control over the encryption keys, for they are generated and stored within the organization’s infrastructure. |
Integration | The cloud provider has access to the encryption keys and has the ability to revoke or rotate them. This might lead to a break in the security framework. | The encryption keys are retained within the organization’s premises, providing enhanced security and performance. |
Dependency | Here, organizations depend on a cloud service provider for key management operations. | The organization holds full responsibility for the encryption keys. |
Thus, the comparison analysis presents a brief overview of both BYOK and HYOK. Choose the encryption model that best aligns with your business operations, needs and goals.
Best Practices of BYOK
As we near the end of the blog, let’s address a few BYOK best practices that can help organizations have advanced BYOK techniques to enhance their security, operational, and compliance aspects.
Security Best Practices
- Make use of cryptographically strong and robust key generation methods that are hard to crack.
- Rotate keys on a regular basis and add expiration policies for sensitive keys, reducing their overusability.
- Develop backup and recovery procedures for keys to restore in case of data loss or system failure.
- Secure encryption keys using algorithms mentioned in security standards so they are vulnerable to cryptographic attacks.
- Encrypt data using the encryption keys before storing or transmittin
Operational Best Practices
- Plan and design integration methods aligned with application type and service provider platform.
- Establish clean and clear key management policies
- Automate key management operations according to key usage and performance.
- Limit user access using strong authentication measures
- Use a centralized key management system only to manage encryption keys across the organization.
Compliance and Governance Best Practices
- Gain a thorough understanding of data protection compliance and regulations pertaining to your location.
- Use logging and monitoring tools that help with the regular maintenance of audit logs.
- Classify data based on criticality and sensitivity to apply appropriate encryption policies and procedures.
- Develop and maintain an incident response plan specific to key management and encryption-related incidents.
- Define contractual agreements and service-level agreements (SLAs) that address key management and data protection requirements.
Conclusion
To conclude, data security is a critical aspect of today’s digital world. Having greater control over data integrity, data sovereignty and compliance adherence for organizations utilizing a shared environment is quite challenging and complex. The BYOK implementation has helped organizations navigate this complex landscape by providing ownership of encryption keys that play a major role in securing and protecting applications and data residing in a public cloud infrastructure. With control over encryption keys, organizations can track down users trying to break or tamper with the infrastructure. BYOK also assists in maintaining compliance in accordance with data residing locations, minimizing penalties and fines.
Thus, the adoption of BYOK benefits organizations struggling to improve and enhance security protocols and policies, which proved to be a significant add-on where every functionality of the encryption model assists organizations with heightened security and improved operational excellence! Get your hands on this technology that is sure to revolutionize the digital world!